Tracing ASIC Fingerprints to Reshape Our Understanding of Bitcoin Mining - Report
"This paper introduces a methodology for determining the market share of every major Bitcoin mining machine, or ASIC, by analyzing nonce patterns and incorporating data sourced from real-world ASICs."


- The report provides a best-guess estimate for Bitcoin network hashrate by ASIC model:
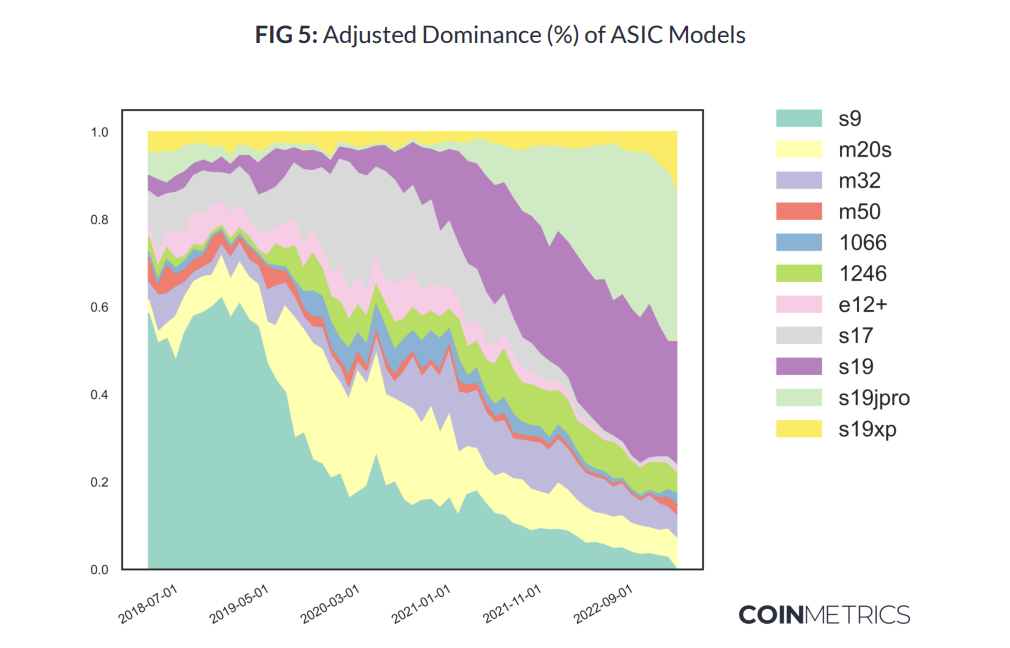
- "Bitmain’s sustained dominance in the hardware market is the first thing to stick out."
- "The surprising resilience of the S9, which officially premiered in 2016 and only recently dropped below the threshold for detectability is also notable. This can be contrasted with the rapid decline of the S17, a notoriously non-performant machine with a large fraction of malfunctioning units due to a design flaw in its control board."
- "Also of note is the rapid rise in dominance of the S19jPro and related models, in contrast to the anemic initial growth of newer models like the S19XP (which was overpriced for an extended period after release and has also suffered from design flaws) and the M50 in the ongoing bear market."
- "This plot can also be represented in terms of total hashrate, which makes the gradual attrition in S9 dominance even more visible."
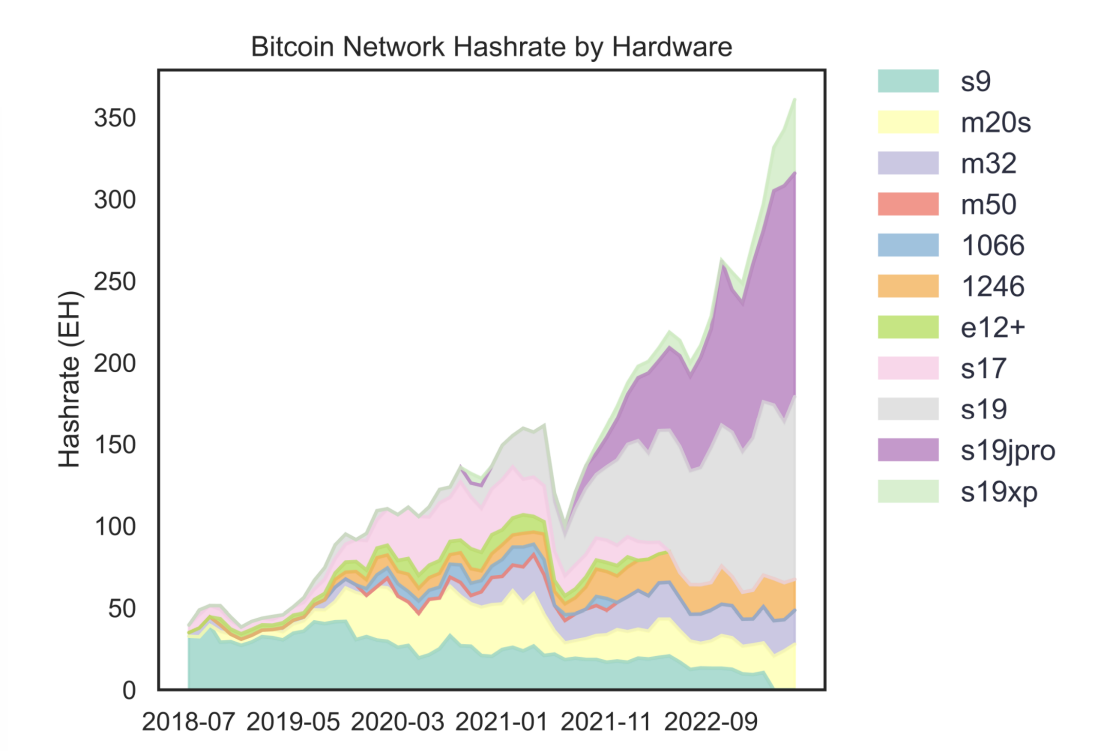
- "This metric is not without its flaws: in particular, it’s unreliable for models with very little hashrate online, since these will mine fewer blocks and as a result won’t leave their characteristic fingerprints on the network as visibly."
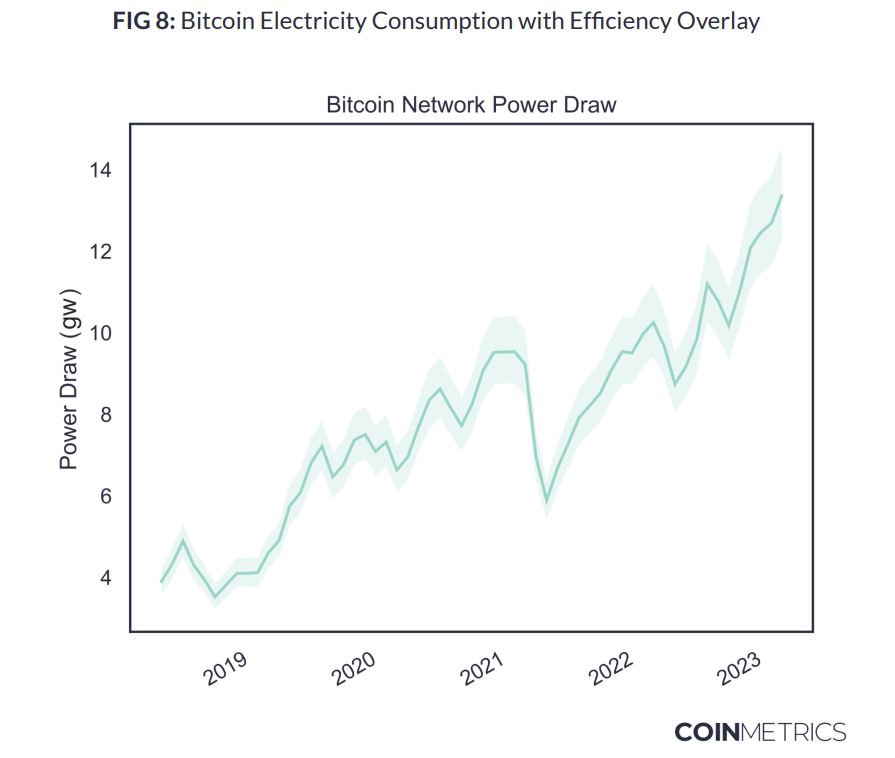
- "With our estimates for the occurrence of each hardware model, it’s straight-forward to estimate a network-wide average efficiency by multiplying the distribution by manufacturer-specified hardware performance, giving us an average value in J/TH."
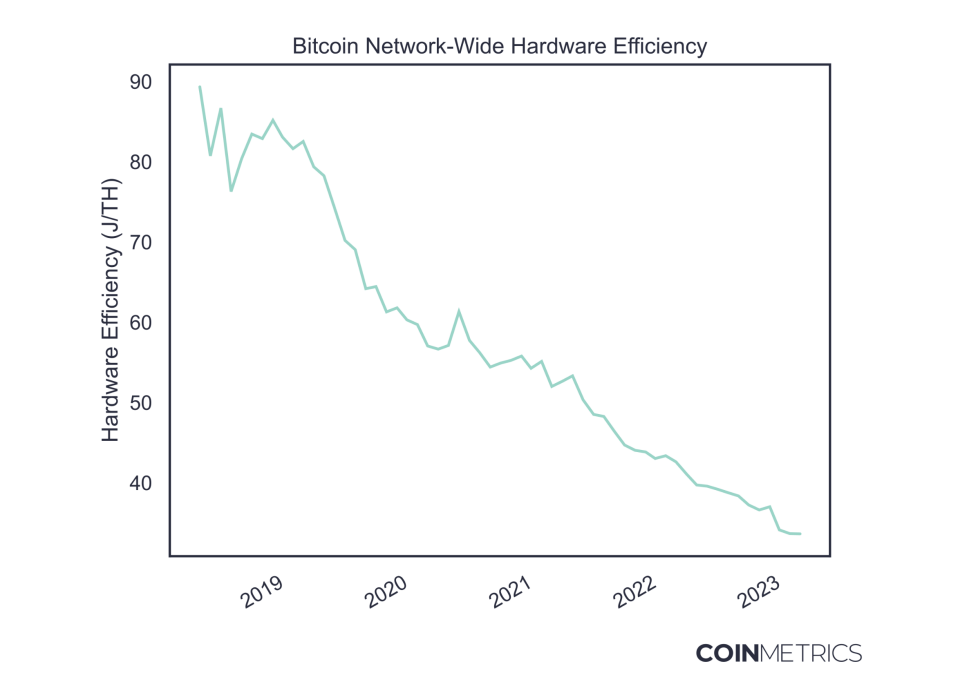
- "A miner’s location on the efficiency curve is a major component in determining their profitability under volatile market conditions."
- "To derive an energy consumption estimate, we simply multiply the network-wide average efficiency by network hashrate."
- "With our hardware distribution, we can come up with a simple heuristic to estimate e-waste: after the then-all-time-high hashrate produced by a certain type of hardware, assume every drop is caused by machines falling permanently offline; then, compare this figure to the manufacturer-specified hashrate and weight per machine to see how much e-waste has been produced."