Huobi Data Breach 'Almost' Leaked KYC Information of 4960 'Whale' Users
Huobi accidentally exposed a set of credentials that enabled access to the crypto exchange’s cloud storage, putting user data at risk for prolonged period of time.

- "Crypto exchange Huobi quietly fixed a data breach that had reportedly put users’ assets at risk since June 2021," wrote The Block.
- The breach involved the exposure of credentials granting write privileges to all of Huobi's AWS S3 buckets, which the company uses for its cloud storage, said white hat hacker and citizen journalist Aaron Phillips in a now deleted blog post.
- "Anyone with access to the credentials could have modified content on Huobi's domains, including huobi.com and hbfile.net. Additionally, user data and internal documents were also at risk of exposure, Phillips said."
- "The incident this time involved the leakage of user contact information on a small scale (4,960 individuals)," Huobi said in an email to The Block.
"The OTC data mentioned in the article is not real transaction data, but test data; user information leaks only involve 4,000 users; the log shows that only white hat has downloaded, and white hat has also stated that he has deleted. Therefore no leakage is actually caused," according to Huobi's updated response.
- "Using the credentials Huobi leaked, I was able to access customer relationship management (CRM) reports containing user information. The reports I found had the contact information and account balances of “crypto whales.” Whales are wealthy users who own a lot of cryptocurrency, and Huobi was clearly interested in creating relationships with them. The company seems to sort these users by their Power Levels. Users with more power to move markets were given higher rankings. In total, Huobi leaked contact and account information for 4,960 users," was stated in the blog post.
- "The type of information leaked does not involve sensitive information and does not affect user accounts and fund security. The incident occurred on June 22, 2021, due to improper operations by personnel related to the S3 bucket in the testing environment of the Huobi Japanese AWS site. The relevant user information was completely isolated on October 8, 2022," claims the exchange.
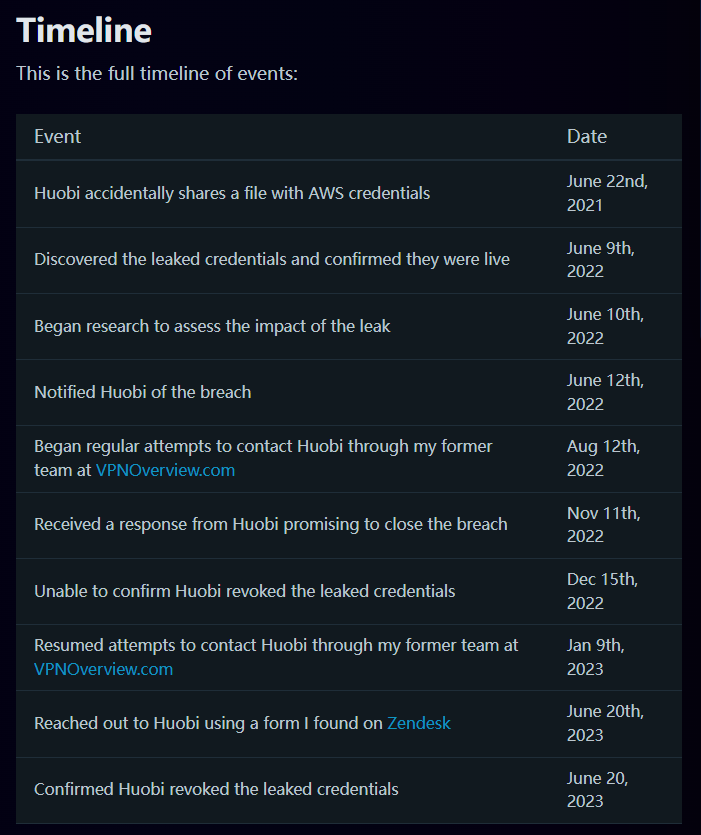
- "It took months for the white hat to receive a response from Huobi, and the leaked credentials remained online even after he first notified Huobi of the issue in June 2022, said Phillips.
Deleted Blog Post
The Block Article / Archive
Huobi's Updated Response




